Introduction
Cybersecurity, professionals are constantly in search of robust tools that can help them evaluate the security of Wi-Fi networks. Fern Wi-Fi Cracker emerges as a powerful and user-friendly solution designed for network security auditing and penetration testing.
Unveiling Fern Wi-Fi Cracker
Fern is a free, open-source Wi-Fi analyzer that runs on a variety of platforms. With its graphical user interface, Fern makes it straightforward for IT security analysts to conduct advanced wireless assessments. Unlike some of its command-line counterparts, Fern simplifies the process of detecting and exploiting vulnerabilities within the Wi-Fi network infrastructure.
Core Features of Fern
Fern is renowned for its ability to crack and recover WEP/WPA/WPS keys. It automatically runs reconnaissance to identify the active WEP, WPA, and WPS networks in range and then leverages popular tools like Aircrack-ng to penetrate the networks. Fern can also use brute force attacks against WPA and WPS keys when necessary and supports multiple session capture and restoration functionalities.
Let’s walk through it
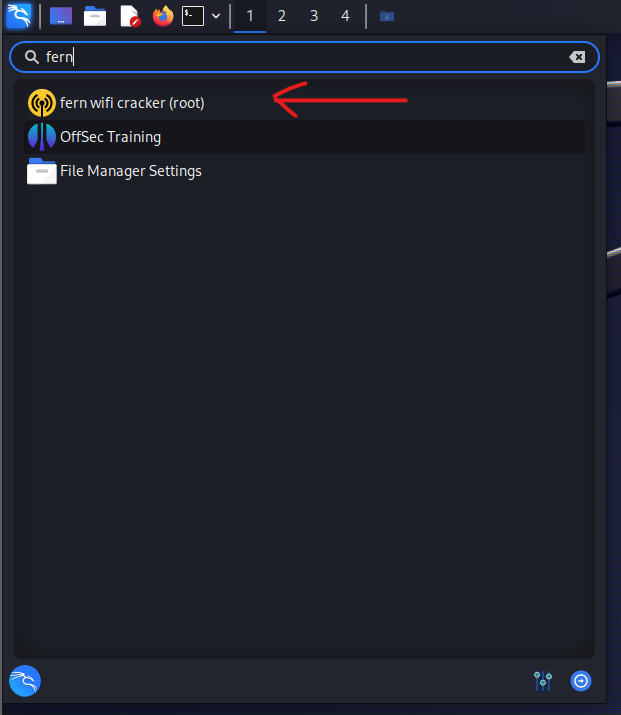
First, let’s fire up our trust in Kali VM. As soon as Kali boots go up to the top left-hand corner and type in Fern and click Fern Wifi Cracker (root).
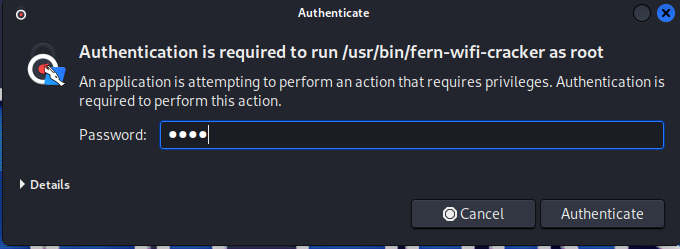
After you click Fern, you’ll be presented with an authentication dialog box. Put in your password and click Authenticate.
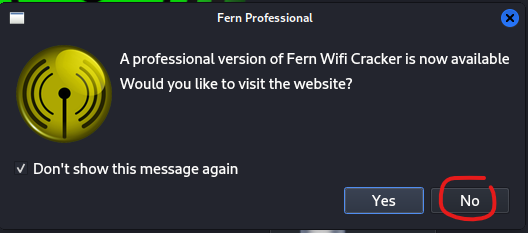
The Fern professional dialog box will pop up next. Just click do not show this message again and click No.
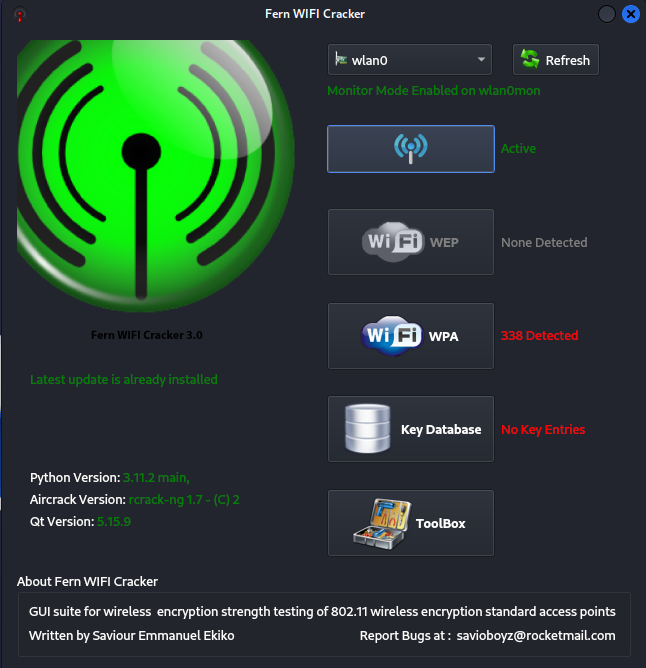
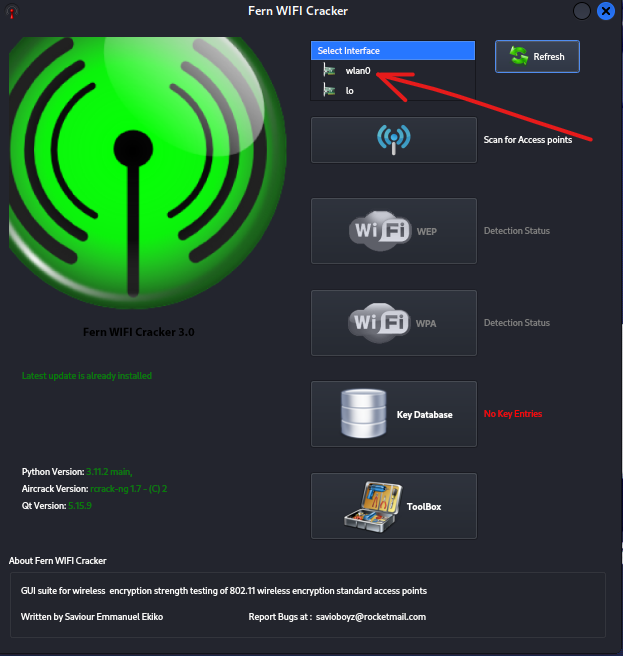
Next the Fern WIFI Cracker dialog box will appear. At the top of the dialog box is the wireless adapter selection. Click the drop-down and select wlan0. This puts the interface into monitor mode.
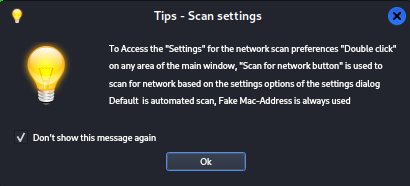
After you put firm into monitor mode, you’ll see a tips dialog box appear. Just click. Don’t show this message again and click OK.
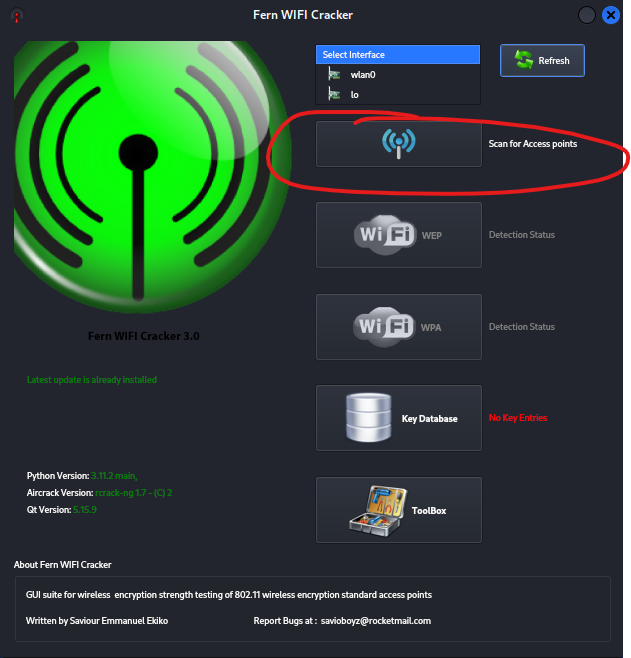
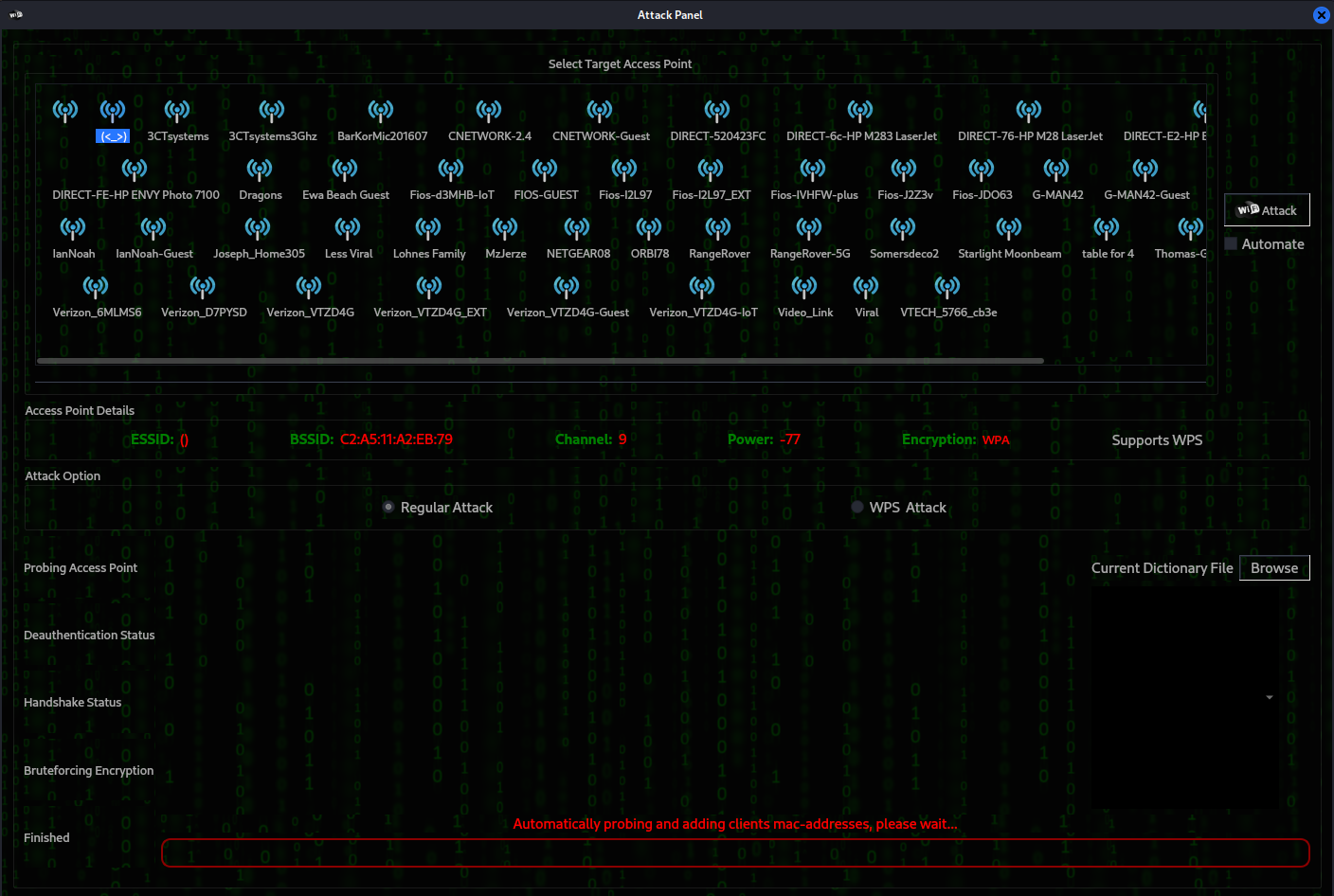
Next in the fern wifi cracker dialog box click scan for access points. This will create a list of potential targets that you can audit. The scanning may take a minute or two.
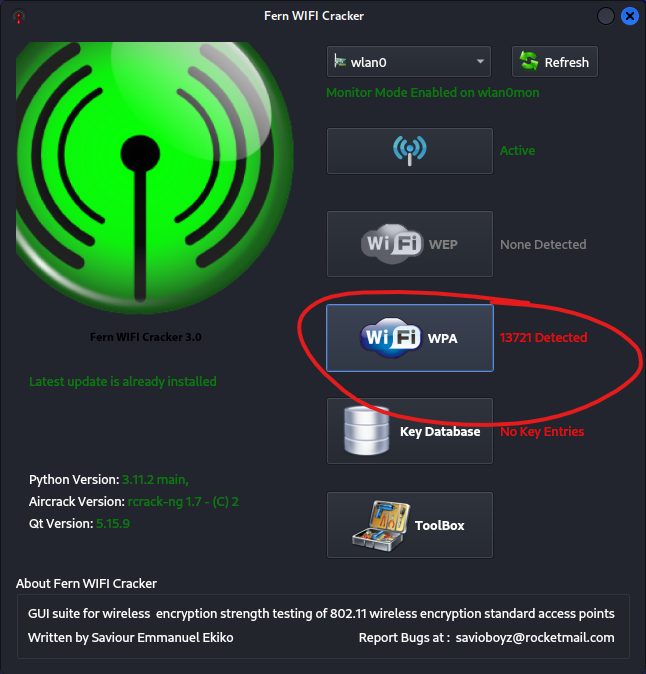
After a minute or two, Fern will pick up a list of potential access points for auditing. As you can see below, the Wi-fi WPA button has 13721 wireless access points detected. I honestly don’t know if this is accurate or not. But I can only assume that it will display access points that are close enough to audit. Click the WIFI WPA button and let’s move on
From the attack dialog box, Fern will show you a list of active wireless access points.
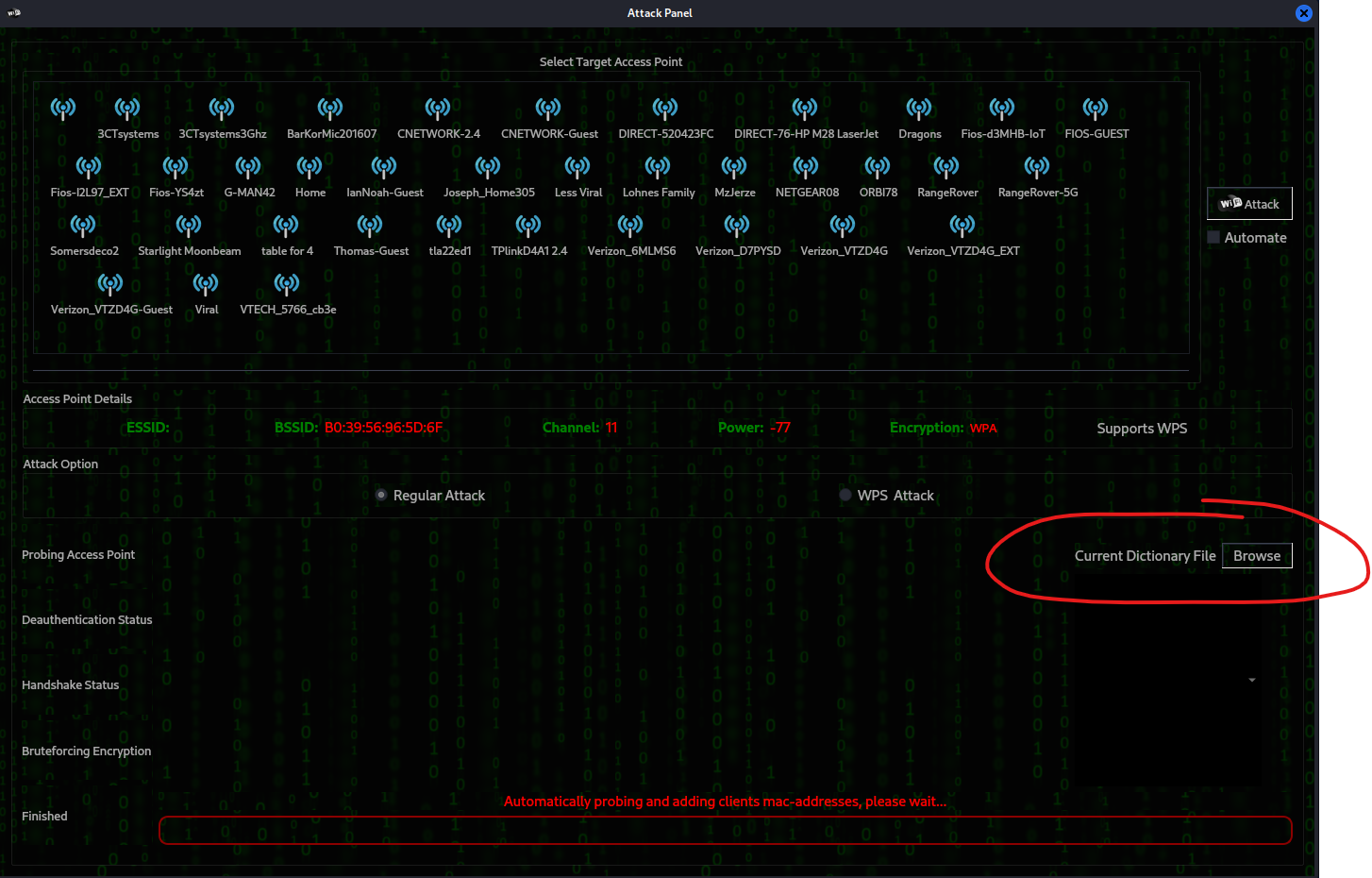
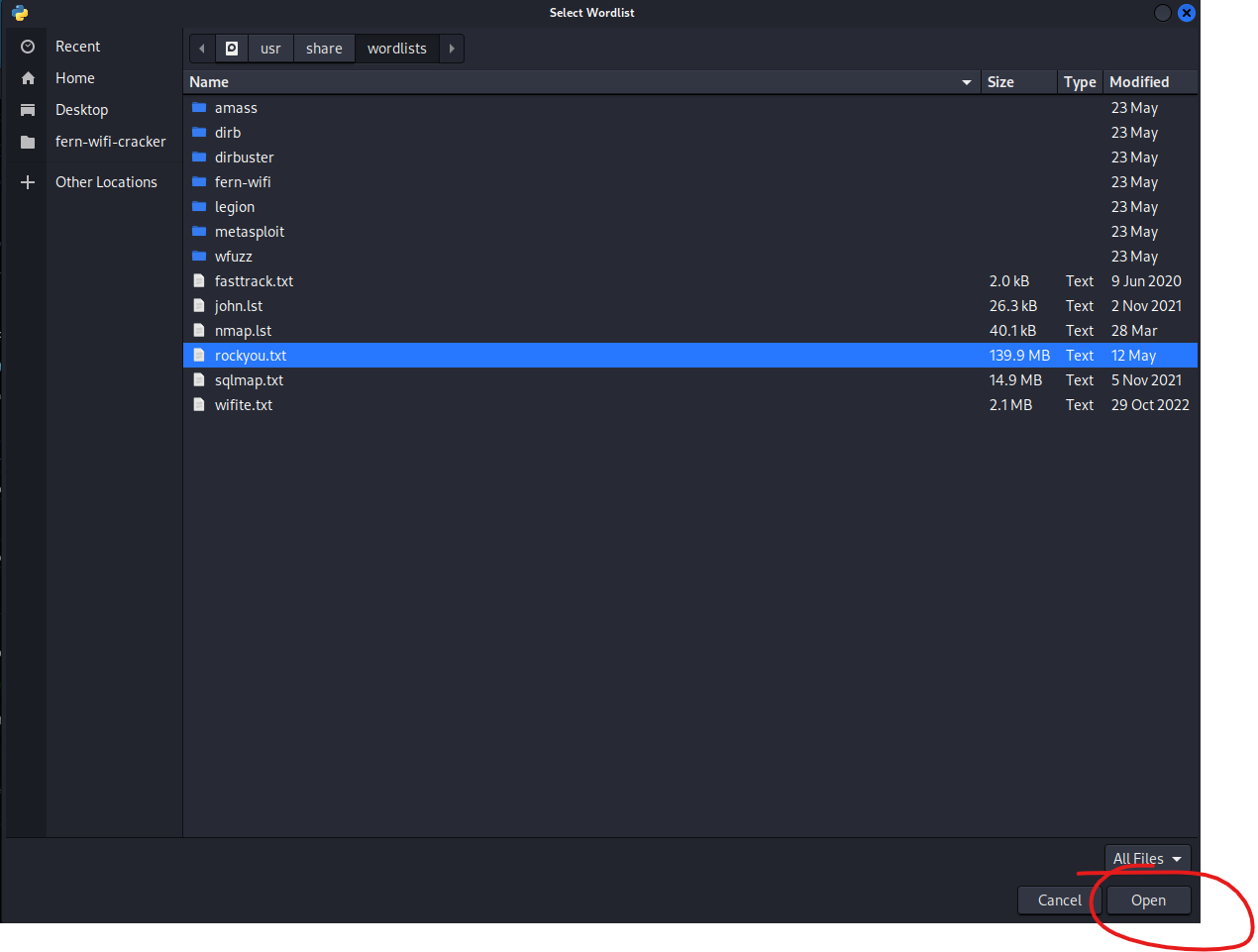
Now, in order to crack anything, you need a dictionary word list. Fern comes with a dictionary wordlist however, it’s rather limited. The most popular word list by far is the rockyou.txt file. The rockyou.txt wordlist is a plain text file that contains a list of over 14 million commonly used passwords that were previously leaked in data breaches. It is commonly used by hackers and professional wireless auditors to crack a file or password. Let’s go get it. Fortunately, Kali comes with the rockyou.txt word list. Click Brows and let’s browse to the following location and load it up.
Browse to the following location to load up rockyou.txt
/usr/share/wordlists/rockyou.txt
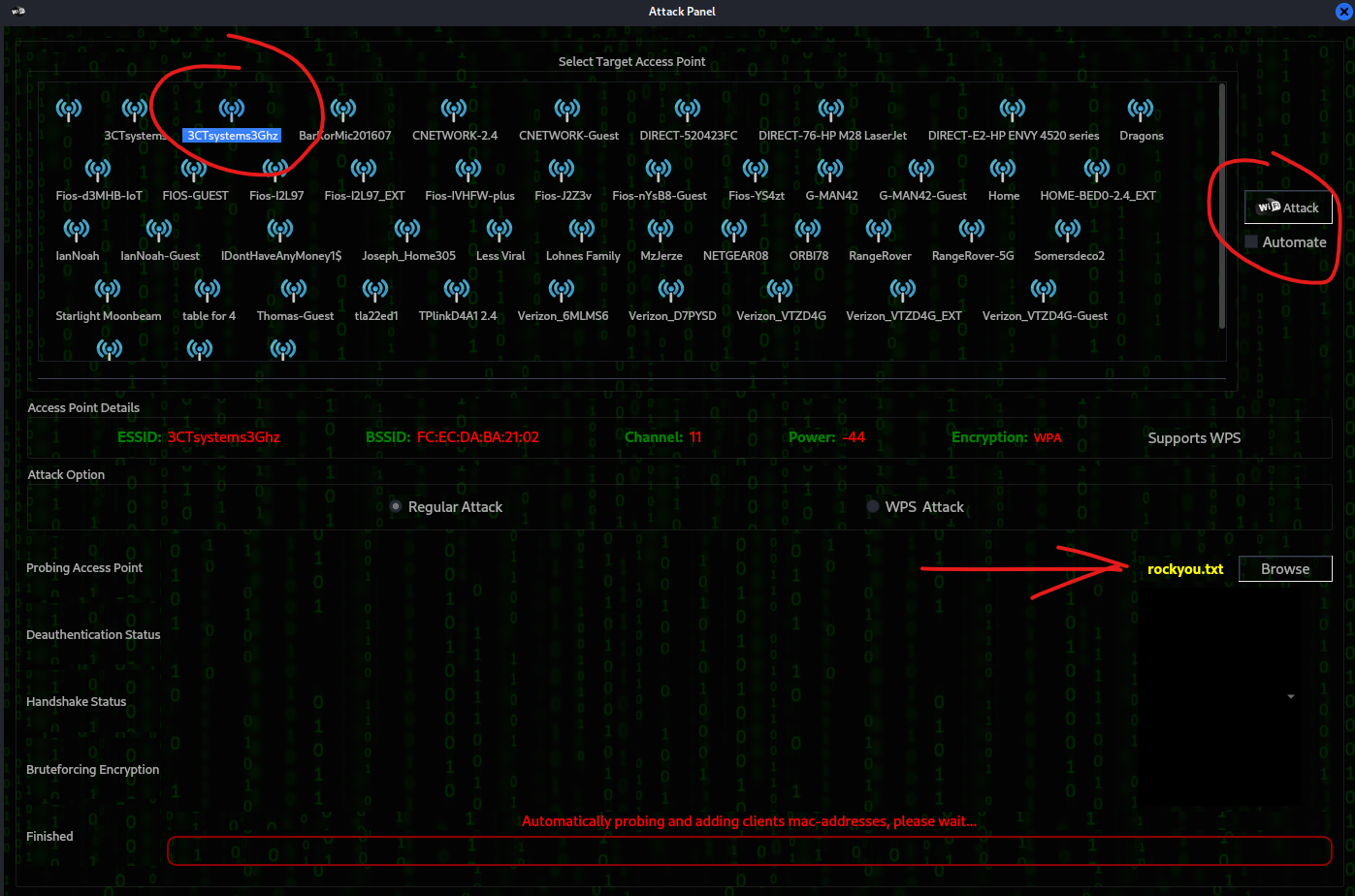
After you have loaded the rockyou.txt wordlist you can see that it is loaded because it is highlighted in yellow next to the browse button. Click the access point that you want to audit and on the right-hand side click Attack to start the attack on the access point.
Now just sit back and chill. Go and get a cup of coffee, do some studying. Currently, what Fern is doing is grinding through the dictionary list that you provided, and depending on the processing power (cpu allocation) that you’ve allocated to your virtual machine, it may take some time. Now This might be a good time to recognize the fact that the free version of Fern does not utilize GPU resources. If I’m not mistaken, the paid version does support GPU acceleration. There are other programs that do this out of the box, however, Fern is not one of them.
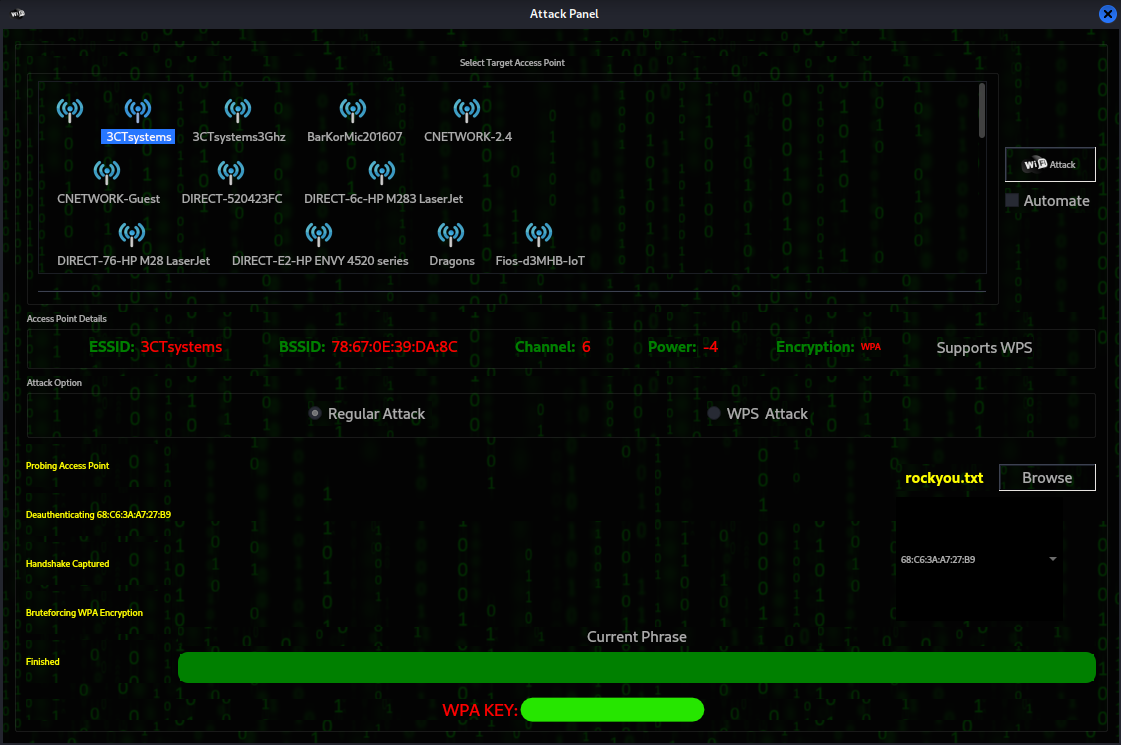
All right, at this point, it looks like Fern did its job. As you can see, the WPA key is displayed at the bottom. I had to cross it out because well, I’m not giving out my SSID password. What’s important to note here is that if the password is in the dictionary file, it’s going to get cracked. That’s why you see these massive dictionary files out there that are fifteen gigs in size. It’s not a matter of if it’s a matter of if its a matter of when and if you’ve got a badass video card, it’s going to happen quickly. How fast is hard to say, but generally it’s days, hours, and minutes.
This might be a good opportunity to talk about the complexity of passwords and length. It looks like 16 Characters is pretty safe nowadays. However, with the advent of quantum computing, it basically blows everything out of the water, I mean everything. I have an article here that talks about quantum computing here.
Advantages Over Other Tools
One of Fern’s significant advantages is its GUI, which stands out in a field crowded with command-line interfaces. This makes it accessible not only to seasoned professionals but also to those who are newer to the field of cybersecurity. Moreover, it integrates various third-party tools and scripts to provide a seamless and comprehensive auditing experience.
The Price Point
The accessibility of Fern is further amplified by its price point. As an open-source tool, it is available at no cost, which allows for widespread use and contribution from the community. This collective development and improvement process ensures that Fern stays up-to-date with the latest in Wi-Fi security.
A Word of Caution
It should be noted that while Fern is powerful, it also requires a foundational understanding of network security to be used effectively. Misuse of such tools can lead to severe legal consequences and ethical violations.
Conclusion
Fern Wi-Fi Cracker exemplifies the tools needed by cybersecurity professionals in an era where Wi-Fi security is paramount. With its ease of use, comprehensive features, and strong community support, Fern is a go-to for those dedicated to bolstering network security and integrity. As the cybersecurity landscape evolves, tools like Fern become invaluable for proactive defense and education in the vast field of network security.