Dominion Cyber Articles

Search...

The Lazarus Group
Introduction In the complex and ever-evolving domain of cybersecurity, few entities have garnered as much attention and intrigue as the Lazarus Group, a shadowy hacking collective believed to originate from North Korea. Renowned for their audacious cyberattacks and alleged state sponsorship, this enigmatic group has emerged as a formidable adversary on the global stage. Recognizing the gravity of the threat posed by North Korean hacking groups, the United States has adopted a multifaceted and comprehensive approach to counter their actions. In this in-depth exploration, we will delve into the Lazarus Group’s origins, motivations, and notable attacks, while examining the nuanced components of America’s cyber strategy and assessing the far-reaching global implications of these efforts. The Lazarus Group: Origins, Motivations, and
Demystifying Malware Analysis: Tools and Techniques for Decoding Advanced Threats.
# Demystifying Malware Analysis: Tools and Techniques for Decoding Advanced Threats Malware analysis is the process of examining and understanding the behavior and purpose of malicious software. This information is crucial for organizations to detect, prevent, and mitigate the risks posed by malware. In this article, we’ll discuss the key tools and techniques used in malware analysis, accompanied by code examples. ## Static Analysis This is the process of inspecting the code without executing it. Here’s how: ### 1. **File Identification Tools:*** **File**: To check basic file details.* **PEiD**: To determine if the file is packed. “`bash$ file suspicious.exe“` ### 2. **Hashing Tools:*** **MD5, SHA-1, or SHA-256**: To get a unique identifier for the file. “`bash$ md5sum suspicious.exe“` ### 3.

Best Practices for Patch Management: Keeping Systems Updated and Secure
Patch management plays a critical role in maintaining the security and functionality of computer systems. It involves the process of applying updates, or patches, to software, operating systems, and firmware to address vulnerabilities and ensure that systems are up to date. Implementing effective patch management practices is essential for keeping systems secure and protected against potential cyber threats. Creating a patch management strategy is the first step towards a proactive approach. This involves identifying the systems and software in need of patching, prioritizing patches based on their criticality, and setting a timeline for deployment. Regular vulnerability scans should be performed to identify any weaknesses that need to be addressed. Establishing a testing environment is crucial before deploying patches to production

Adaptive Authentication Balancing Security and User Experience in Modern Applications
Adaptive authentication is a crucial element in modern applications, striking a balance between security and user experience. In today’s digital landscape, where cyber threats are ever-evolving, it has become essential to implement robust authentication mechanisms while ensuring a seamless and user-friendly experience for individuals. Adaptive authentication adapts and adjusts security measures based on various factors such as user behavior, context, and risk levels. The security vs. user experience balancing act is a persistent challenge for developers and organizations. On one hand, strong authentication measures are imperative to protect sensitive data and prevent unauthorized access. On the other hand, user experience plays a vital role in ensuring convenience, accessibility, and user satisfaction. Striking the right balance between these two aspects is
Recon-ng: The Ultimate Guide to Footprinting and Web Reconnaissance
Key Takeaway: Recon-ng is a powerful tool for footprinting and web reconnaissance: It provides a comprehensive suite of modules and techniques to gather information about a target, enabling security professionals to assess vulnerabilities and potential attack surfaces. Installing and setting up Recon-ng is straightforward: By following the installation instructions, security professionals can quickly have Recon-ng up and running on their system, ready to perform reconnaissance tasks. Effective utilization of Recon-ng modules is essential: By understanding the categorization and exploration of modules, security professionals can efficiently gather information such as subdomains, open ports, email addresses, and social media profiles, aiding in the reconnaissance process. Advanced techniques and best practices enhance reconnaissance outcomes: By leveraging advanced techniques such as automated scans, exploiting
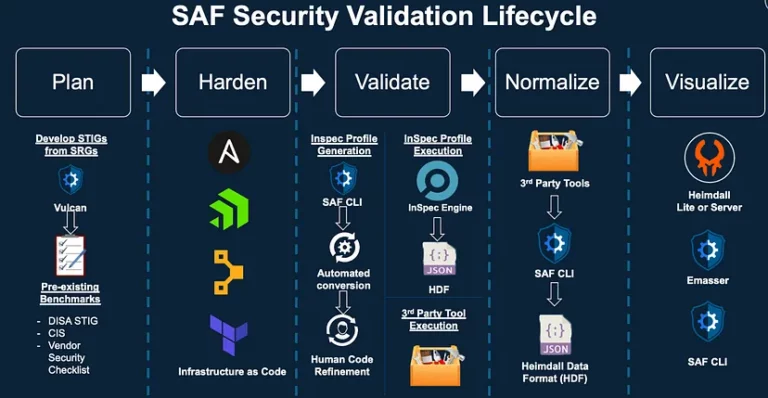
Automating Vulnerability Management Tools and Strategies for Continuous Security Assessments
Continuous security assessments are of utmost importance in today’s rapidly evolving digital landscape. With new vulnerabilities and threats emerging regularly, organizations need to ensure that their systems and networks are secure and protected at all times. Automating vulnerability management has become a crucial aspect of maintaining a robust security posture. Vulnerability management refers to the process of identifying, evaluating, and mitigating vulnerabilities in a system or network. By automating this process, organizations can efficiently and effectively analyze their systems for potential weaknesses, prioritize remediation efforts, and stay proactive in addressing security risks. There are several reasons why automating vulnerability management is essential. Firstly, manual assessments are time-consuming and prone to errors, whereas automation allows for scalability and consistency. Automation enables
Blockchain and Cybersecurity Beyond Cryptocurrency Securing Modern Digital Transactions
Blockchain technology has gained significant attention with the rise of cryptocurrencies like Bitcoin. However, its applications extend far beyond digital currency. In the modern digital age, cybersecurity is of paramount importance, and blockchain offers a promising solution to secure digital transactions. This article explores the intersection of blockchain and cybersecurity, going beyond cryptocurrency to understand the potential and benefits of blockchain in securing various industries. To begin, we need to grasp the basics of blockchain technology. Understanding its decentralized and immutable nature provides a foundation for comprehending its role in cybersecurity. It is also crucial to recognize the importance of cybersecurity in the digital age, where data breaches and cyber threats are prevalent concerns. Moving beyond cryptocurrency, we delve into

Honeypots and Honeynets Deception Techniques in Cyber Defense
Honeypots and honeynets are powerful deception techniques used in cyber defense to detect and analyze cyber threats. Understanding these techniques is essential for organizations to strengthen their security measures. Here, we will explore the concept of honeypots and honeynets, their functionalities, benefits, types, and the challenges involved in their implementation. 1. What are Honeypots and Honeynets? Honeypots are decoy systems or resources designed to lure attackers and gather information on their tactics and techniques. Honeynets are networks of interconnected honeypots that provide a larger-scale environment to deceive and detect cyber threats. 2. How do Honeypots and Honeynets Work? Deployment and Configuration: Honeypots and honeynets are strategically placed within a network to attract potential attackers. Simulation of Vulnerabilities and Services: These

Decentralized Identity Management Securing User Identity in a Fragmented Digital World
In a fragmented digital world where individuals interact with various online platforms and services, user identity management plays a crucial role in maintaining privacy, security, and trust. The challenges of traditional identity management approaches, such as centralized systems, have paved the way for decentralized identity solutions. Decentralized identity, also known as self-sovereign identity, is an emerging concept that aims to provide individuals with greater control and ownership over their digital identities. It operates on the principles of privacy, security, and user consent. Decentralized identity works by leveraging technologies like blockchain to enable secure and verifiable interactions between users, service providers, and other entities. It eliminates the need for centralized authorities and offers several advantages over traditional systems. The advantages of

The Rise of Fileless Malware Detection and Countermeasures
As technology continues to advance, so do the tactics used by cybercriminals. One such method that has gained prominence in recent years is fileless malware. This article explores the rise of fileless malware, its detection, and countermeasures to mitigate this growing threat. Fileless malware, as the name suggests, is a type of malicious software that operates without leaving traces of files or executables on the victim’s system. It is designed to exploit vulnerabilities in the operating system or legitimate applications, making it difficult to detect and remove. Unlike traditional malware, fileless malware resides in the computer’s memory, registry, or scripts, allowing it to evade traditional antivirus software. Understanding how fileless malware works is vital in combating this cyber threat. It
