Introduction
Welcome to our guide on cracking WEP and WPA encryption protocols. In this article, we will delve into the world of wireless network security and explore the vulnerabilities present in these commonly used encryption methods. By understanding the weaknesses and employing the right tools and techniques, one can gain unauthorized access to protected Wi-Fi networks. However, it is crucial to note that engaging in such activities without proper authorization is illegal and unethical.
Understanding WEP and WPA
Before we dive into the intricacies of cracking WEP and WPA, let’s first understand what these encryption protocols are. WEP, or Wired Equivalent Privacy, was the standard security protocol for Wi-Fi networks in the early days. However, it has proven to be highly vulnerable to various attacks due to its weak encryption algorithm.
WPA, short for Wi-Fi Protected Access, was introduced as a more secure alternative to WEP. It aimed to address the shortcomings of its predecessor by implementing stronger encryption algorithms and improved security features.
Common vulnerabilities in WEP and WPA
Both WEP and WPA have their fair share of vulnerabilities that make them susceptible to attacks. Although WPA is considered more secure than WEP, it is still not completely immune to exploitation. Some common vulnerabilities include:
- Brute force attacks: Attackers attempt to guess the encryption key by systematically trying all possible combinations.
- Dictionary attacks: Attackers use precomputed tables of possible passwords, known as “rainbow tables,” to crack the encryption.
- WiFi Protected Setup (WPS) vulnerabilities: WPS, a feature designed to simplify the process of connecting devices to Wi-Fi networks, can be exploited to gain unauthorized access.
Let’s take an in-depth look at the tools and techniques for cracking WEP and WPA.
Cracking WEP and WPA encryption involves leveraging various tools and techniques. One widely used tool is Aircrack-ng, which combines several attack methods to exploit the vulnerabilities present in the WEP and WPA protocol. However, leveraging modern-day tools is a much more realistic process and saves a lot of time. Tools such as Kismet, Fern, Wi-Fi Cracker, and WiFight can also aid in the process. Let’s fire up our trustee-old Kali box and see what kind of mischief we can get into.
Starting Kismet
Every wireless engagement should begin with a good bit of Recon. Kismet is a wireless network and device detector, sniffer, wardriving tool, and WIDS (wireless intrusion detection) framework. It is generally not used to crack WEP and WPA. But it’s a great tool for recon of wireless networks. I would refer you here for more information.
Kismet works with Wi-Fi interfaces, Bluetooth interfaces, some SDR (software-defined radio) hardware like the RTLSDR, and other specialized capture hardware.
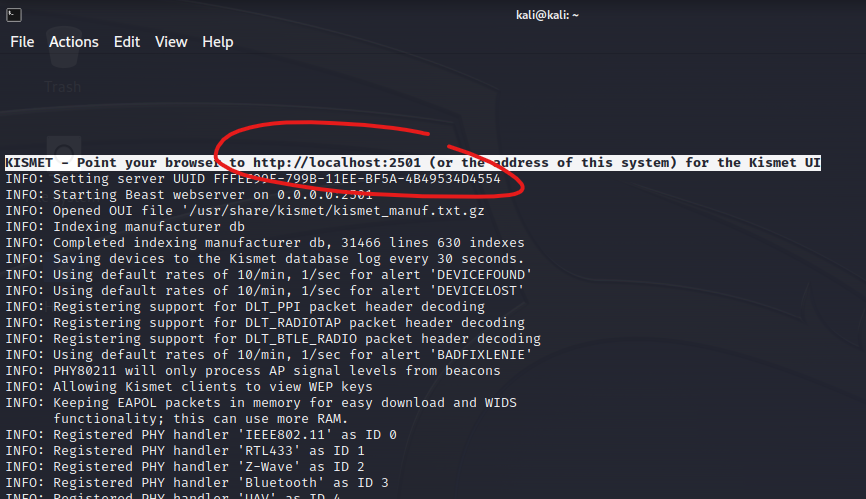
All right, let’s jump right in. The easiest way to get started is to open up a command prompt in Kali Linux and type in the following in the command prompt.
$ sudo kismet
After you start Kismet it will direct you towards a web page running on. http://localhost:2501
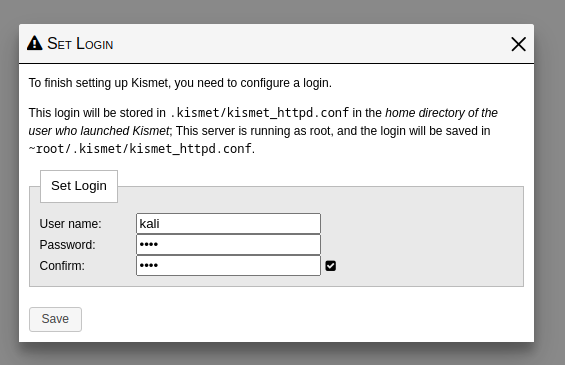
Setting Login
After you open up the web browser proceed to http://localhost:2501. After you hit enter, it will present you with the login screen. Put in your username and password and click save. I’m using the default Kali username and password. It’s a VM and I’m going to destroy it after I’m done here. Don’t hate.
After logging in, you’ll be presented with a welcome screen. Just click continue and move on.
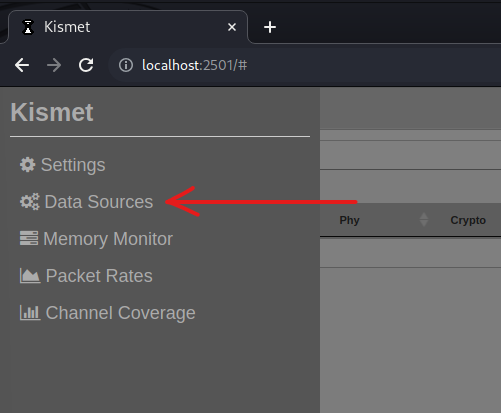
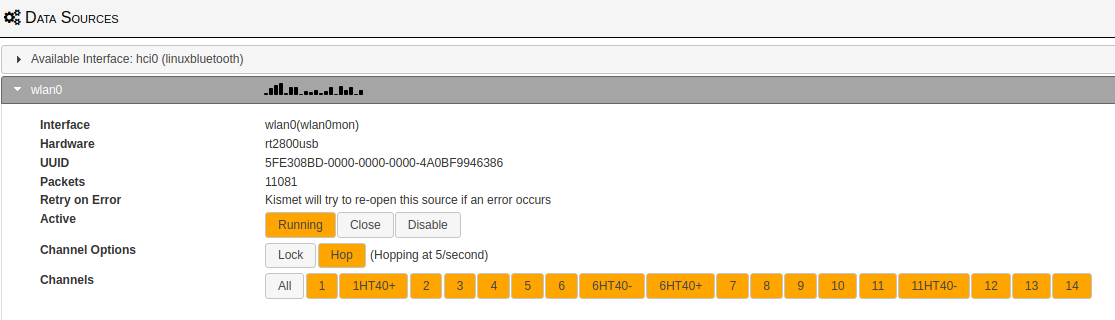
Data Sources
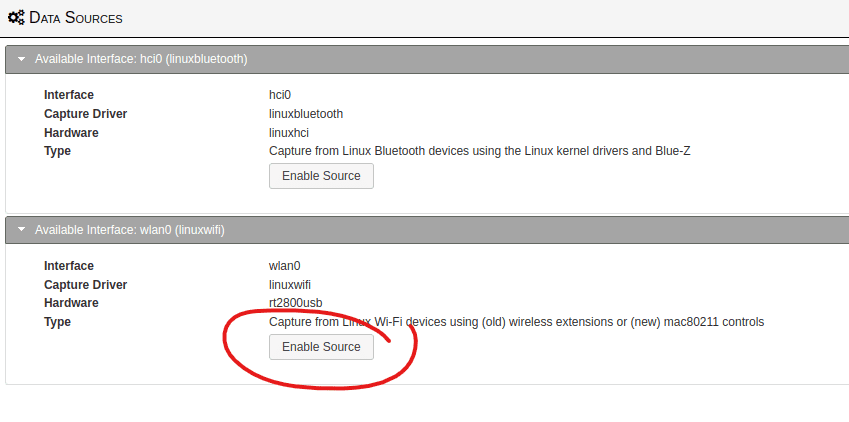
Open the upper left-hand corner click the hamburger icon and choose Data Sources. At this point, I have taken for granted that you already have a wireless access card that’s capable of promiscuous mode. If you already have one, you should be good to go. If you don’t, then have a look at this post here. Moving on. Once you click Data Sources, it will show you the wireless cards that are available for capture. Find your wireless card and click Enable Source for your wireless card.
Enable Source Adapter
Find your adapter and click enable source.
Wireless Channels
After enabling your wireless device, you’re presented with what channels to capture. Currently, I am capturing all channels. Do the same and you will be good to go, unless you have a specific reason for not capturing a certain channel, It’s best to just capture all at this time.
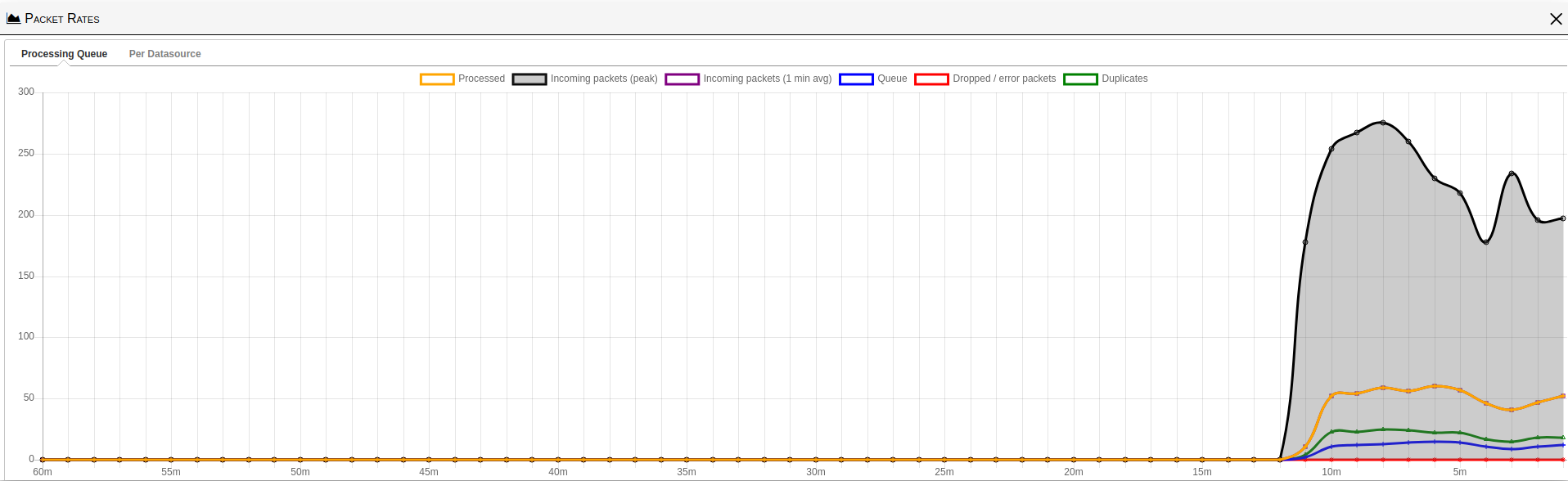
Packet Rates
Just below the Data Sources is the Kismet packet rates dialog box. This feature is the Kismet wireless network detector, sniffer, and intrusion detection system that provides real-time statistics on packet rates, which are essential for monitoring network performance and identifying unusual traffic patterns that could signify potential threats. This dialog box typically displays the packets per second (pps) rates for various packet types, such as management frames, control frames, and data frames. It may also offer insights into the number of packets captured, missed, or dropped, thus serving as a valuable tool for IT professionals in the cybersecurity industry to analyze the health and security of a wireless network. The packet rates can be indicative of the network’s usage load, interference issues, or possible malicious activity if there are unexpected spikes in traffic.
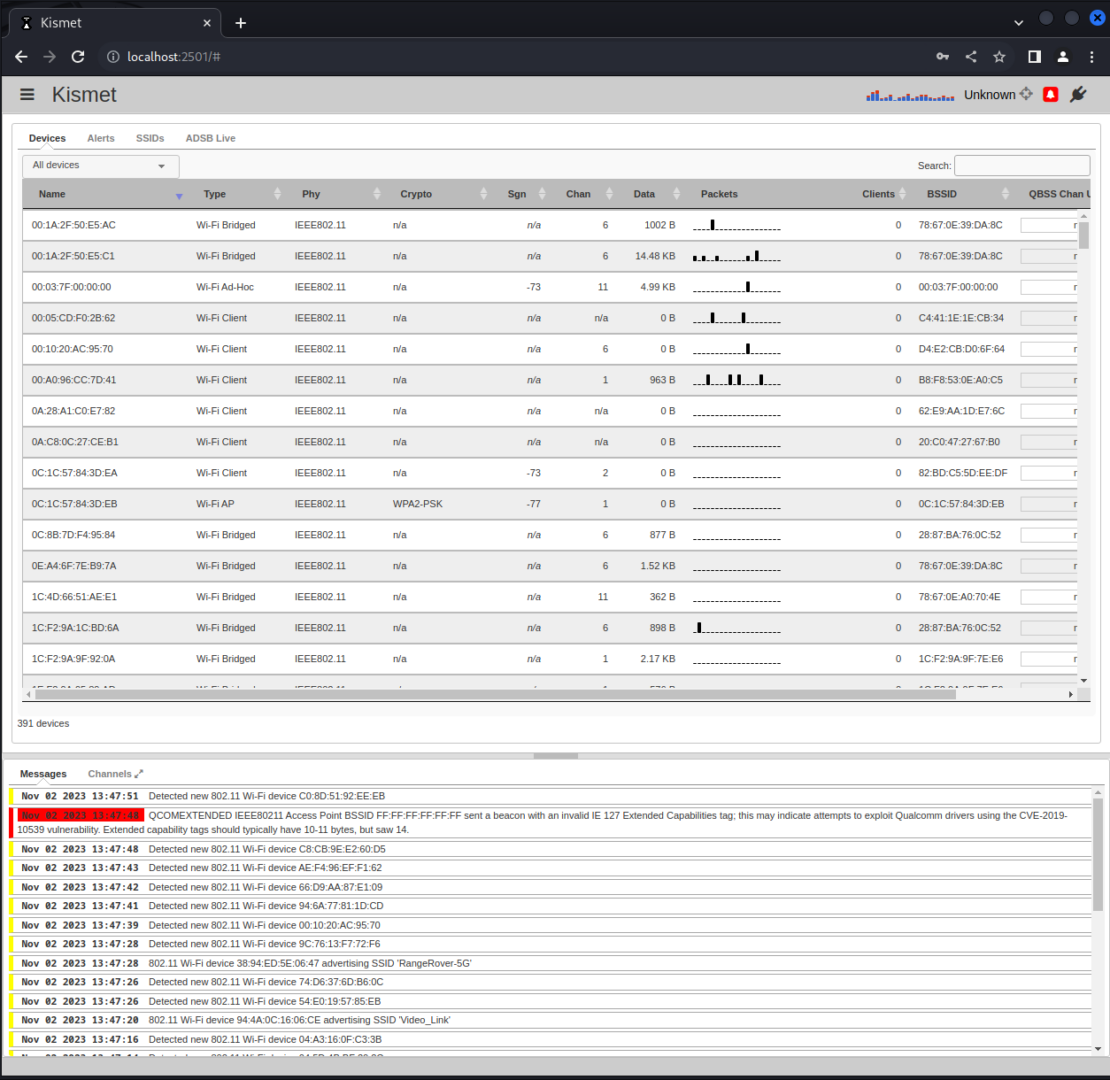
Devices
As you can see below Kismet is collecting information passively on any network that is within range. Kismet’s devices dialog box is an integral feature for IT professionals, especially those involved in network monitoring and analysis. It provides a comprehensive list of all detected devices within the wireless network’s range. This includes information such as the MAC addresses, the names of the devices (if available), the signal strength, the type of device (e.g., access point, client), and the networks they are associated with. The dialog box also offers filtering and sorting capabilities to manage the displayed information efficiently. This allows for a granular view of the network’s device ecosystem, aiding in the identification of unauthorized devices, the assessment of network coverage, and the detection of potential security vulnerabilities or breaches. For cybersecurity experts, this dialog box is a gateway to understanding the landscape of the wireless spectrum they are tasked with securing.
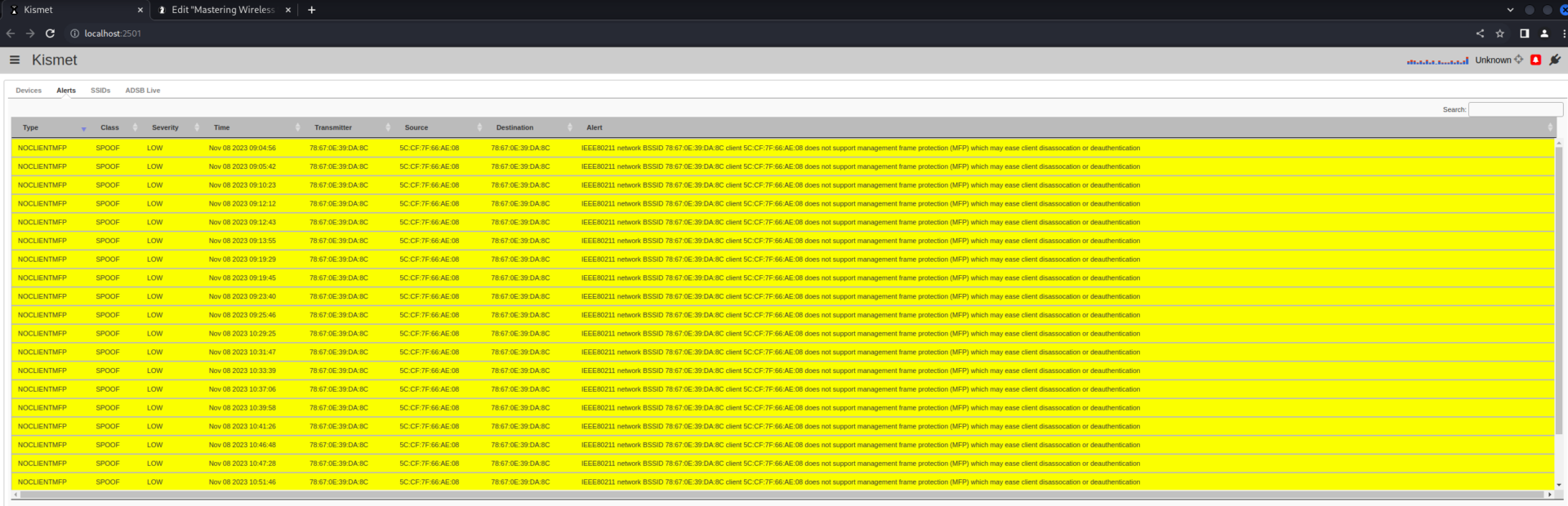
Alerts Dialog Box
Kismet’s alerts dialog box is a critical component for cybersecurity professionals, designed to notify the user about potential network security events detected by the Kismet system. This dialog box displays a list of alerts triggered by various anomalies or patterns that could indicate suspicious activities, such as unexpected network traffic, the use of default passwords, the presence of rogue access points, or unusual probes and attacks. Each alert provides details such as the time of detection, the type of alert, the severity, and the involved network or device. This allows IT and cybersecurity specialists to quickly assess and respond to potential threats. The alerts are customizable and can be configured to match specific network environments or threat models, providing a tailored security monitoring solution.
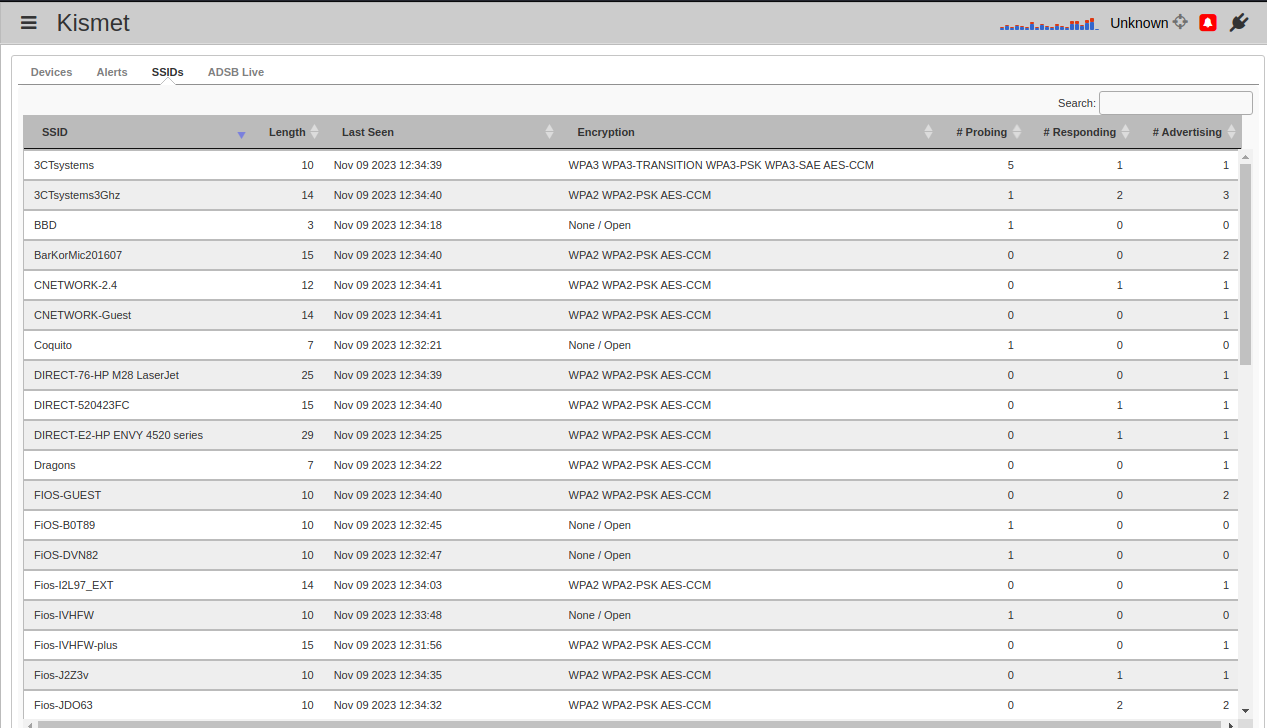
SSIDs Dialog Box
The SSID dialog box in Kismet is a specialized interface that presents detailed information about the Service Set Identifiers (SSIDs) of wireless networks detected by the tool. It is a vital feature for cybersecurity and IT professionals to analyze the wireless landscape. This dialog box lists all the SSIDs, including hidden or non-broadcasted ones, encountered during the monitoring process. It often provides additional details such as the encryption type, the channel number, the signal strength, and the number of devices connected to each SSID. The SSID dialog box aids in identifying networks, assessing their security configurations, such as the use of weak encryption methods, and spotting potential rogue access points or networks that may be spoofing legitimate SSIDs to conduct malicious activities. This function is essential for maintaining the integrity and security of wireless networks in a managed environment.
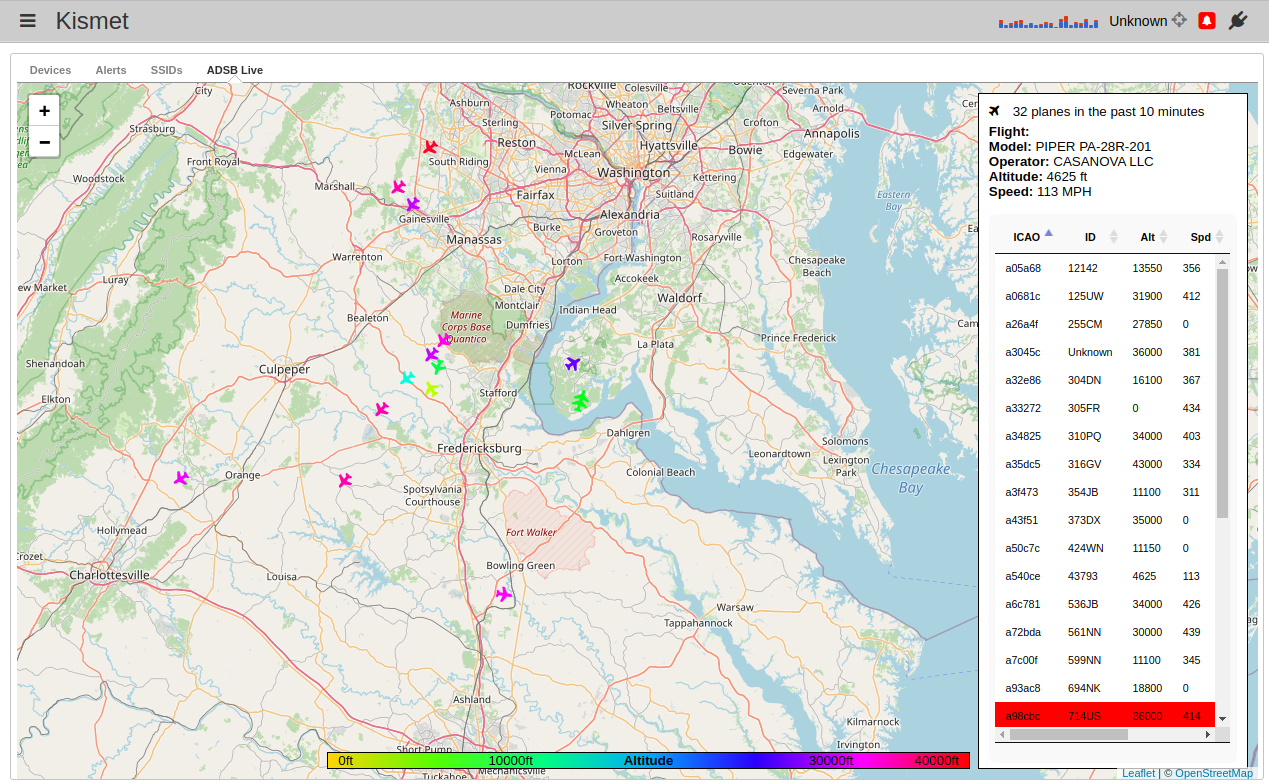
Software Defined Radio and ADS-B
If you’re a total nerd like I am, you might go out and purchase a software-defined radio like this one RTL-SDR (RTL2832U)
An RTL-SDR offers a highly affordable solution for setting up a real-time air radar system. It taps into the ADS-B (Automatic Dependent Surveillance-Broadcast) Mode-S transponders that modern aircraft use to send out their location and altitude data to air traffic control. By picking up these ADS-B signals, one can construct a personal aircraft tracking system right at home. While commercial ADS-B receivers could set you back anywhere from $200 to $1000, the RTL-SDR’s modest price tag of around $20 is particularly appealing for enthusiasts. However, it’s important to mention that for actual in-flight navigation purposes, relying on the RTL-SDR is not advisable due to safety considerations.
Legal and ethical considerations
It is important to highlight that attempting to crack WEP or WPA encryption without proper authorization is illegal and unethical. Engaging in such activities can lead to severe legal consequences. This article is intended for educational purposes only, to raise awareness about the vulnerabilities present in wireless networks and to encourage users to take necessary precautions to secure their Wi-Fi networks.
Protecting your Wi-Fi network
Now that we have explored the vulnerabilities in WEP and WPA, it is essential to understand how to protect your Wi-Fi network. Here are some crucial steps you can take:
- Use strong passwords: Set a long and complex password for your Wi-Fi network.
- Enable WPA2 encryption: Implement the highest level of encryption available for your router.
- Disable WPS: Disable the Wi-Fi Protected Setup feature on your router to eliminate the risk of WPS-related vulnerabilities.
- Regularly update firmware: Keep your router’s firmware up to date to ensure you have the latest security patches.
Conclusion
In conclusion, understanding the vulnerabilities in WEP and WPA encryption protocols is crucial in maintaining the security of your Wi-Fi network. While it is possible to crack these encryption methods using various tools and techniques, it is essential to remember that unauthorized access is illegal and unethical. By taking necessary precautions and implementing robust security measures, you can protect your Wi-Fi network from potential attacks and ensure the safety of your data.
Once again, we emphasize the importance of using this knowledge responsibly and for educational purposes only.